
Table of Contents Link to heading
- Port Numbers
- The Need for Port Addressing
- Socket
- Types of Port Numbers
- TCP/UDP Common Ports
netstatCommand
Port Numbers Link to heading
The Need for Port Addressing Link to heading
Socket Link to heading
A socket pair, consisting of the source and destination IP addresses and port numbers, is also unique and identifies the session between the two hosts.
For example, an HTTP web page request being sent to a web server (port 80) running on a host with an IPv4 address of 192.168.1.20 will be destined to socket 192.168.1.20:80.
Types of Port Numbers Link to heading
The Internet Assigned Numbers Authority (IANA) is a standards body responsible for assigning various addressing standards.
Well-known Ports (numbers 0 to 1023) Link to heading
By defining these well-known ports for server applications, client applications can be programmed to request a connection to that specific port and its associated service.
| Well-known Port | Application | Protocol |
|---|---|---|
| 20 | File Transfer Protocol (FTP) Data | TCP |
| 21 | File Transfer Protocol (FTP) Control | TCP |
| 23 | Telnet | TCP |
| 25 | Simple Mail Transfer Protocol (SMTP) | TCP |
| 69 | Trivial File Transfer Protocol (TFTP) | UDP |
| 80 | Hypertext Transfer Protocol (HTTP) | TCP |
| 110 | Post Office Protocol 3 (POP3) | TCP |
| 194 | Internet Relay Chat (IRC) | TCP |
| 443 | Secure HTTP (HTTPS) | TCP |
| 520 | Routing Information Protocol (RIP) | UDP |
Registered Ports (numbers 1024 to 49151) Link to heading
When not used for a server resource, a client can dynamically select a registered port as its source port.
| Registered Port | Application | Protocol |
|---|---|---|
| 1812 | RADIUS Authentication Protocol | UDP |
| 1863 | MSN Messenger | TCP |
| 2000 | Cisco Skinny Client Control Protocol (SCCP, used in VoIP applications) | UDP |
| 5004 | Real-Time Transport Protocol (RTP, a voice and video transport protocol) | UDP |
| 5060 | Session Initiation Protocol (SIP, used in VoIP applications) | UDP |
| 8008 / 8080 | Alternate HTTP | TCP |
Dynamic/Private/Ephemeral Ports (numbers 49152 to 65535) Link to heading
TCP/UDP Common Ports Link to heading
| Common | Port | Application Port Type |
|---|---|---|
| 53 | DNS | Well-known TCP/UDP common port |
| 161 | SNMP | Well-known TCP/UDP common port |
| 531 | AOL Instant Messenger, IRC | Well-known TCP/UDP common port |
| 1433 | MS SQL | Registered TCP/UDP common port |
| 2948 | WAP (MMS) | Registered TCP/UDP common port |
| 5432 | PortgreSQL | Registered TCP/UDP common port |
netstat Command
Link to heading
A network utility that can identify:
- The protocol in use, the local address and port number, the foreign address and port number, and the state of the connection.
- Active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for IP, ICMP, TCP, and UDP), and IPv6 statistics (for IPv6, ICMPv6, TCP over IPv6, and UDP over IPv6).
Unexplained TCP connections can indicate that something or someone is connected
to the local host, which is a major security threat. Additionally, unnecessary
TCP connections can consume valuable system resources, thus slowing the host’s
performance. Use netstat to examine the open connections on a host when
performance appears to be compromised.
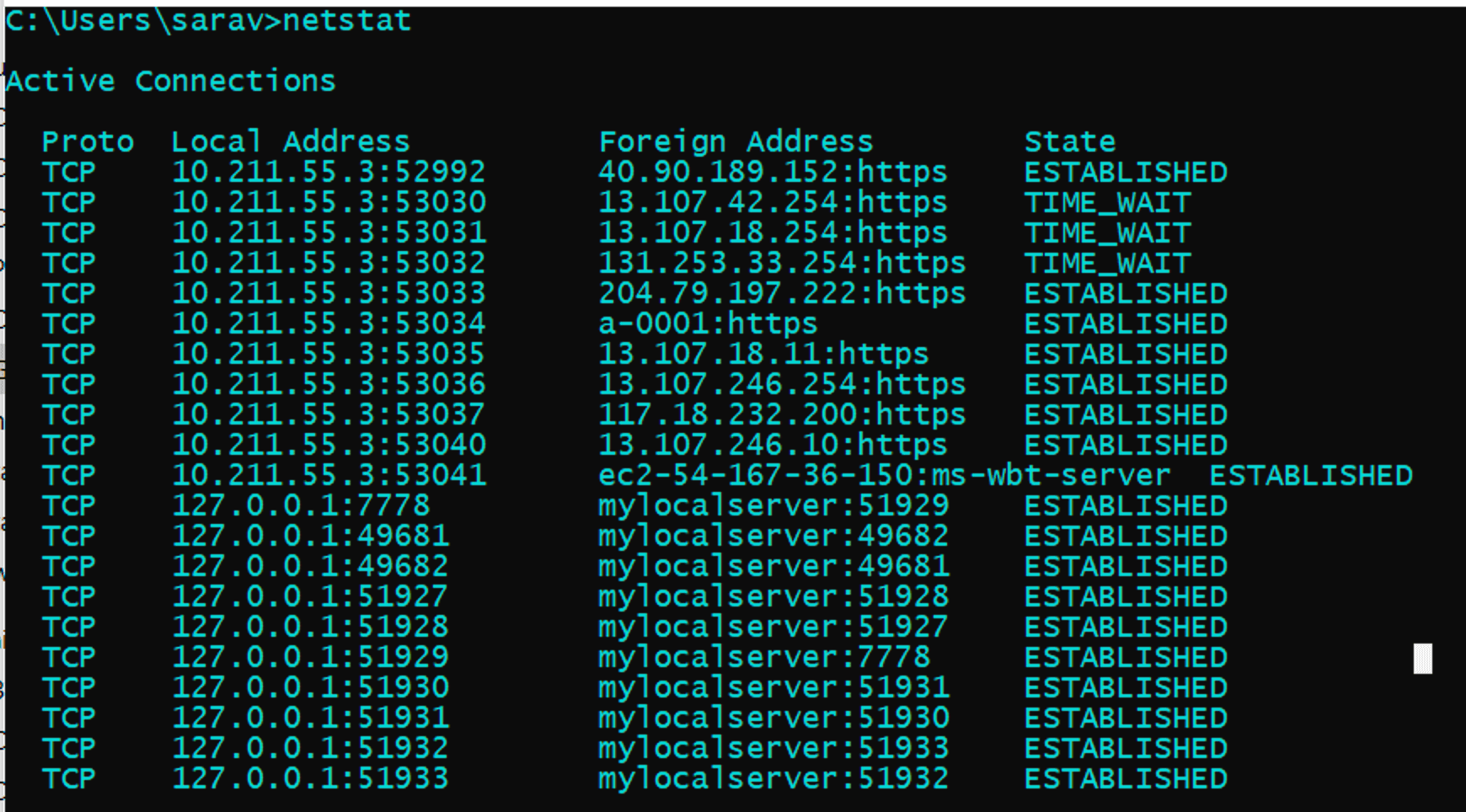
Image Source: Middleware Inventory