Table of Contents Link to heading
- What is PGP?
- How Does PGP Work?
- Why Use PGP?
- Install PGP
- Backup Your PGP Keys
- Import Your Keypair
- PGP Cryptography
- Import Another User’s PGP Key
What is PGP? Link to heading
PGP, short for Pretty Good Privacy, is an encryption program that allows you to secure data and communication through cryptographic methods. Created by Phil Zimmermann in 1991, PGP has evolved into a widely-used standard for email encryption, digital signatures, and file security. At its core, PGP combines public-key cryptography with symmetric encryption, offering a powerful blend of security and ease of use.
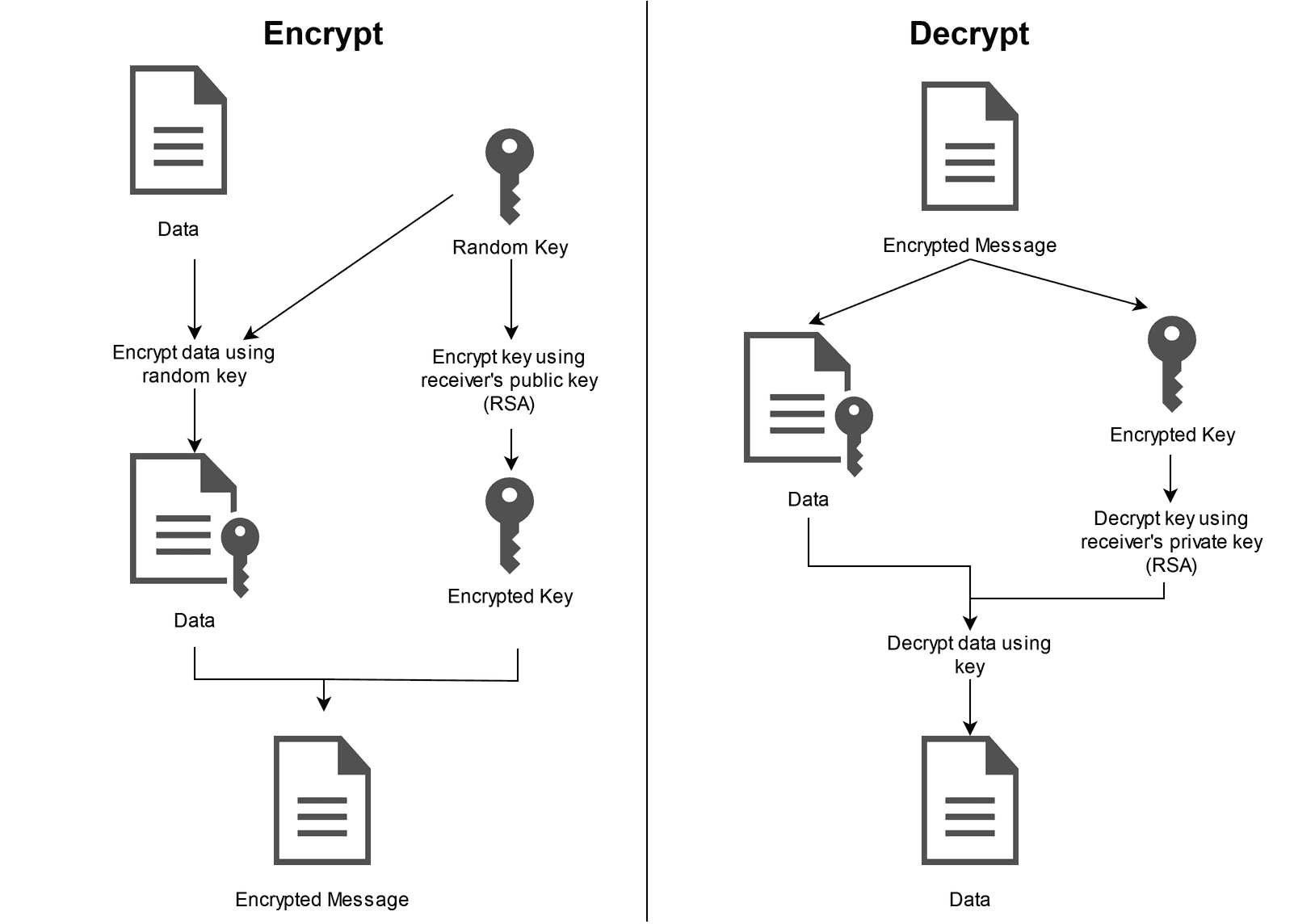
How Does PGP Work? Link to heading
PGP operates on two fundamental principles of cryptography:
- Public-Key Cryptography: Each user has a pair of keys: a public key that can be shared openly and a private key that must be kept secret. The public key is used to encrypt messages, while the private key decrypts them, ensuring that only the intended recipient can read the content.
- Symmetric Encryption: For bulk data encryption, PGP uses a symmetric key generated for each session. This symmetric key is then encrypted with the recipient’s public key, combining speed with strong security.
By leveraging these techniques, PGP enables secure communication even over potentially insecure channels.
Why Use PGP? Link to heading
PGP offers several advantages:
- Data Confidentiality: Messages and files are encrypted, making them unintelligible to unauthorised parties.
- Authentication: Digital signatures verify the identity of the sender, ensuring the message’s authenticity.
- Integrity: Cryptographic checks prevent tampering and ensure the content remains unchanged during transmission.
Install PGP Link to heading
To begin using PGP for encryption and decryption, you’ll need to install the GPG software and generate your keypair.
sudo apt install gpg -y
gpg --full-generate-key
After generating your keypair, you can list the long form of the PGP keys for which you have both public and private keys:
gpg --list-secret-keys --keyid-format=long
Example output:
/home/netadmin/.pgp/pubring.kbx
-------------------------------
sec 4096R/3AA5C34371567BD2 2016-03-10 [expires: 2025-04-19]
uid duke <duke@example.com>
ssb 4096R/4BB6D45482678BE3 2016-03-10
Backup Your PGP Keys Link to heading
Protect your keypair by backing it up securely:
gpg --export --armor <fingerprint> --output pubkey.asc
gpg --export-secret-keys --armor <fingerprint> --output privkey.asc
A fingerprint can be the long form of the PGP key ID or the associated email
address (e.g., duke@example.com).
Archive your private keys:
tar zcvf private-keys.tgz privkey.asc
Encrypt the archive with a master password:
openssl aes-256-cbc -salt -pbkdf2 -in private-keys.tgz -out private-keys.tgz.enc
The encrypted file private-keys.tgz.enc can be publicly shared, as it is
secured by the master password.
Restore the PGP Keys Link to heading
If you need to restore your backup, use the following commands:
wget -P private-keys.tgz.enc &&
openssl aes-256-cbc -salt -pbkdf2 -in ~/.pgp/private-keys.tgz.enc -out ~/.pgp/private-keys.tgz -d &&
tar zxvf ~/.pgp/private-keys.tgz -C ~/.pgp &&
rm ~/.pgp/private-keys.tgz
Import Your Keypair Link to heading
To import your backed-up keypair:
gpg --import pubkey.asc
gpg --allow-secret-key-import --import privkey.asc
If necessary, trust the keys:
gpg --edit-key <fingerprint>
PGP Cryptography Link to heading
Encrypt Messages with GPG Link to heading
Encrypt a file or message using your PGP key:
gpg --armor --sign --encrypt --recipient <name> path/to/file
gpg -a -s -e -r <name> path/to/file
The output file will have the same name as the input file but with an .asc
extension.
Decrypt Messages with GPG Link to heading
Decrypt an encrypted file:
gpg --decrypt path/to/file.asc
gpg -d path/to/file.asc
Import Another User’s PGP Key Link to heading
To import another user’s key, you can retrieve it directly from a key server:
gpg --recv-keys <keyID>
Or search for their key using:
gpg --search-keys <name>